The data obfuscation feature in gradient fox allows your organization to stay compliant by masking sensitive information from the Kafka topic data that users can view. This feature helps your company adhere to policies set forth by your organization and local regulations. The obfuscation settings in gradient fox enable fine-grained control over what data is masked and how the obfuscation is performed.
The obfuscation settings screen allows you to define detailed configuration of the policies that you want to enforce. The obfuscation settings are centered around the concept of obfuscation groups. Each group is meant to enforce a certain policy within your organization, but you can also structure your groups in a different manner as well. You can have as many obfuscation groups as you need to uphold the data protection rules within your company.
During the obfuscation process there is a possibility for errors to occur. For example, the input data is not in the specified format (e.g. not an email address) or the structued value cannot be parsed (e.g. not valid JSON). In those cases, the user will see an error message such as 'Unable to read JSON' instead of the actual data.
By default configured obfuscations will apply to all users and user groups. You can add exclusions to this rule by excluding obfuscation groups from applying to specific
user groups. If a user belongs to a group that has an obfuscation exclusion, then the obfuscation rules of that obfuscation group will not apply and they can
see the topic data in the clear.
You can find more information about this in the User Management
Single Sign-On section of the documentation.
You can add a new obfuscation group using the Add Group button on the Obfuscation-page. It will bring up a dialog where you can enter a unique name for the group as well as a group category. The category can be any string that helps you categorize your obfuscation groups, for example PII, PHI or any other free-form text. After adding the group you must add resources and fields to start enforcing your obfuscation policies.

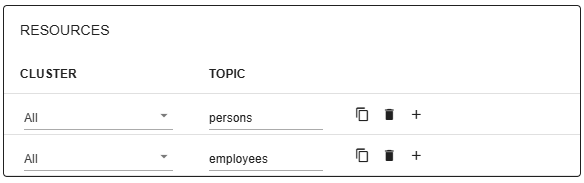
The first task after creating a new group is to specify which topics the group should apply to. In order to do that, you need to configure group resources which define the cluster and the topic name. For the cluster you can also select All, in which case the obfuscation will apply to the specified topic in any cluster you have configured. Notice that a specific topic can only appear in one resource group. The same topic name can appear in two groups as long as the cluster is different.
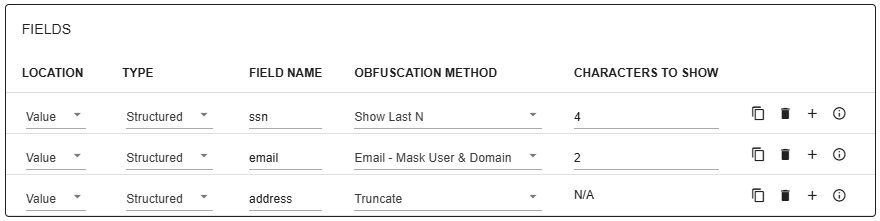
The Fields-section of the obfuscation group defines what exactly is obfuscated and how the data will be obfuscated. First you need to define which part (location) of the message will be obfuscted.
Next you need to specify the format of the data in the given location.
The last step is to define the obfuscation method that will be used to mask the original data.
Example: user@example.com -> ****************
Example: user@example.com -> us**************
Example: user@example.com -> **************om
Example: myuser@example.com -> b4c9a289323b21a01c3e940f150eb9b8c542587f1abfd8f0e1cc1ffc5e475514
Example: user@example.com -> *
Example: user@example.com -> us**************
Example: user@example.com -> user@ex*********
Example: user@example.com -> us**@ex*********